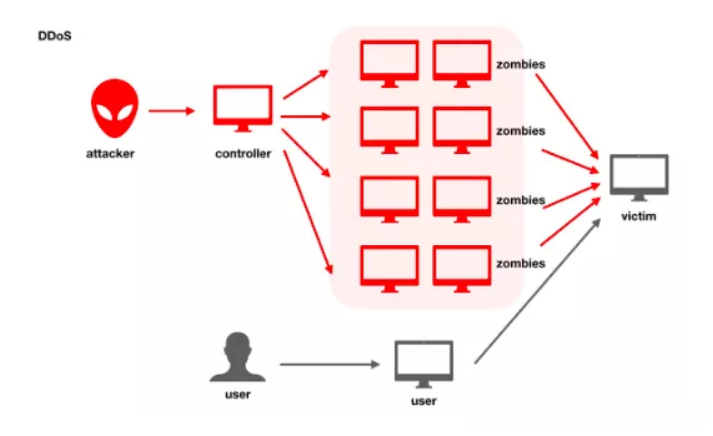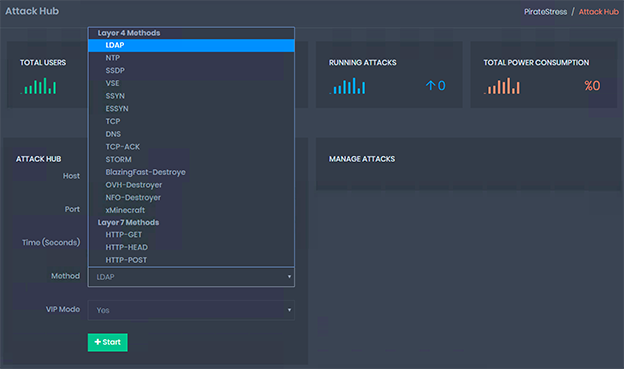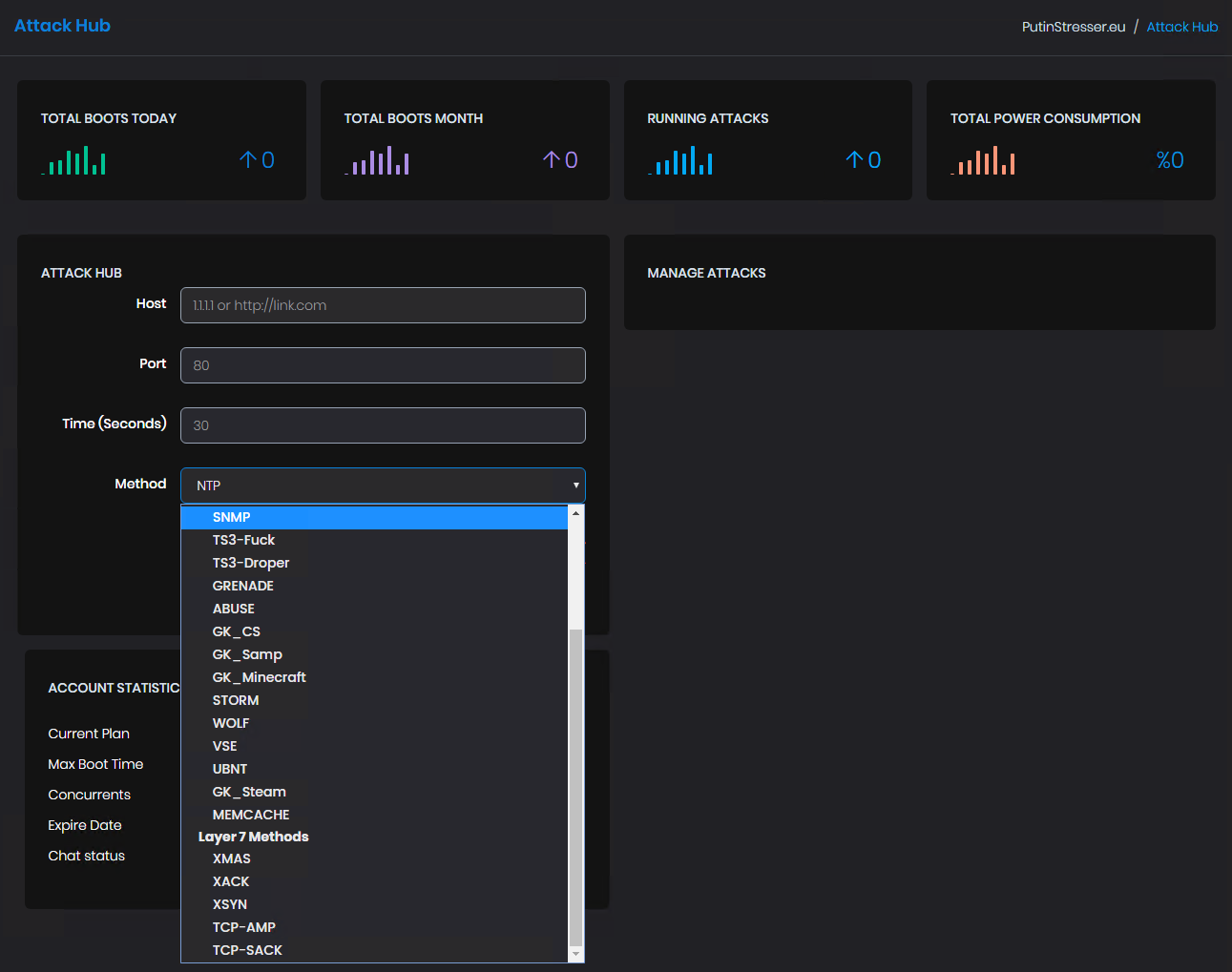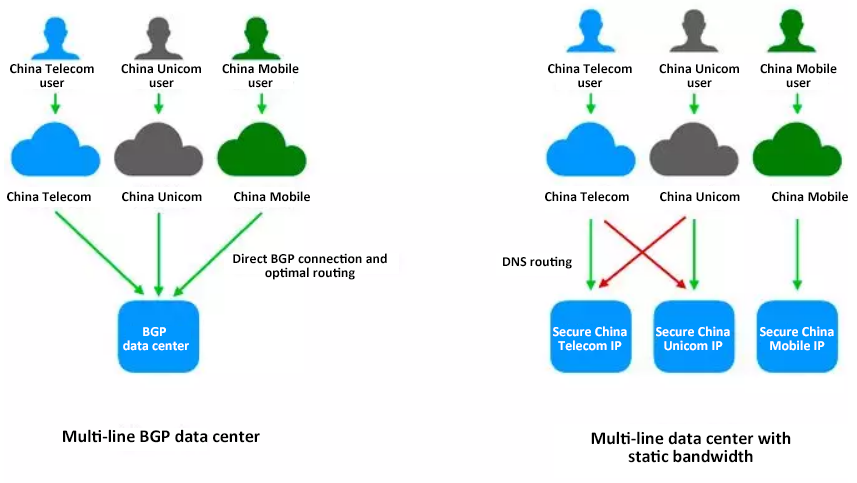
Defending against TB-level Traffic Attacks with Advanced Anti-DDoS systems - Alibaba Cloud Community
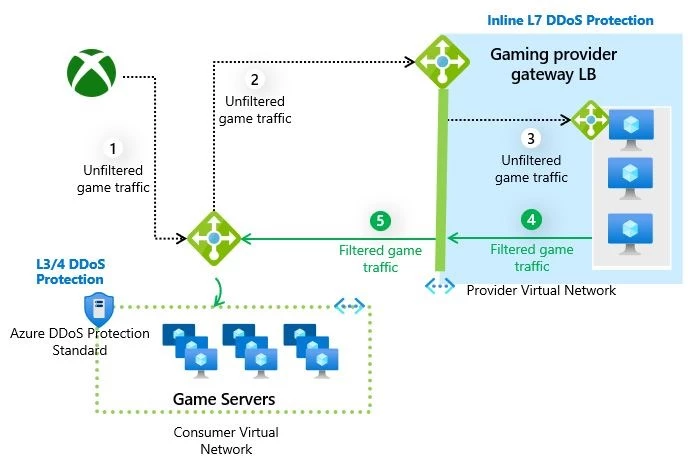
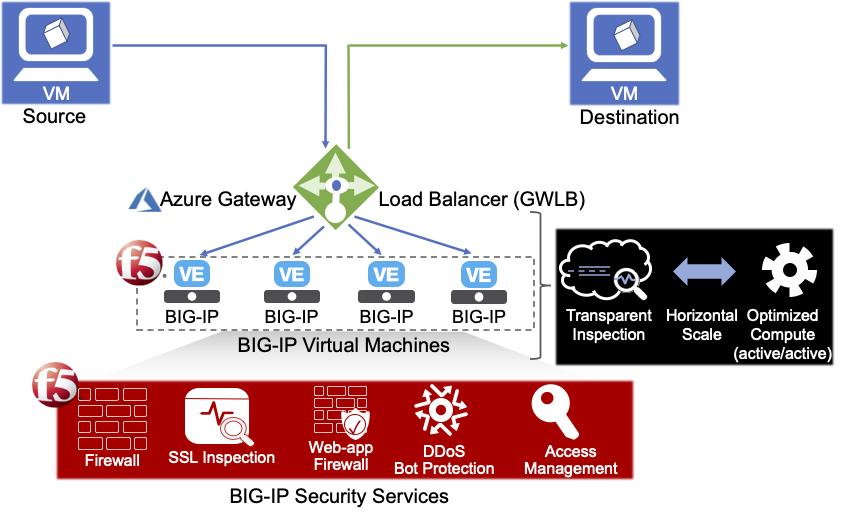
Protect workloads with inline DDoS protection from Gateway Load Balancer partners | Microsoft Azure Blog

Set up an external passthrough Network Load Balancer for multiple IP protocols | Load Balancing | Google Cloud

Figure 3 from Short Paper: IP spoofing detection for preventing DDoS attack in Cloud Computing | Semantic Scholar