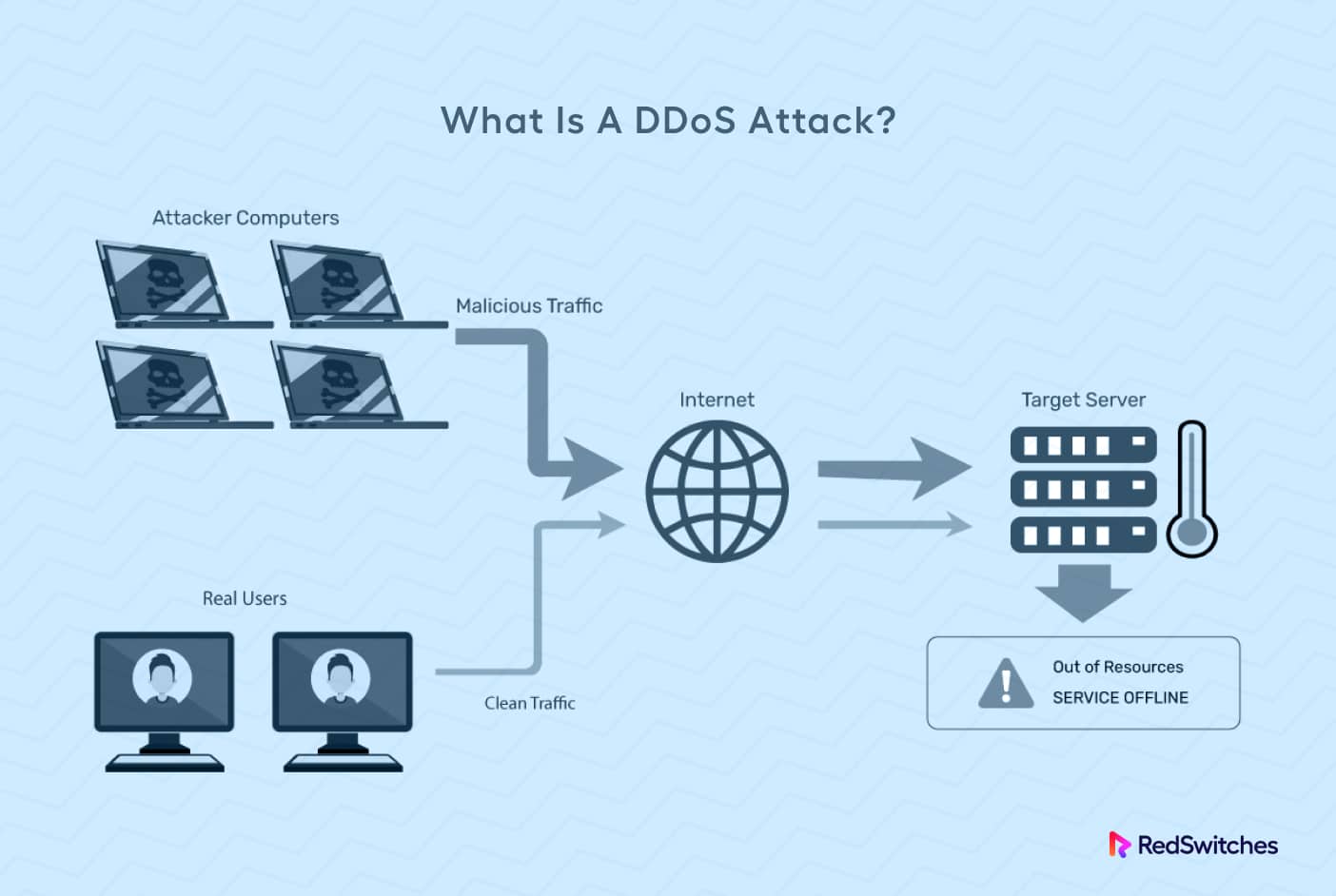
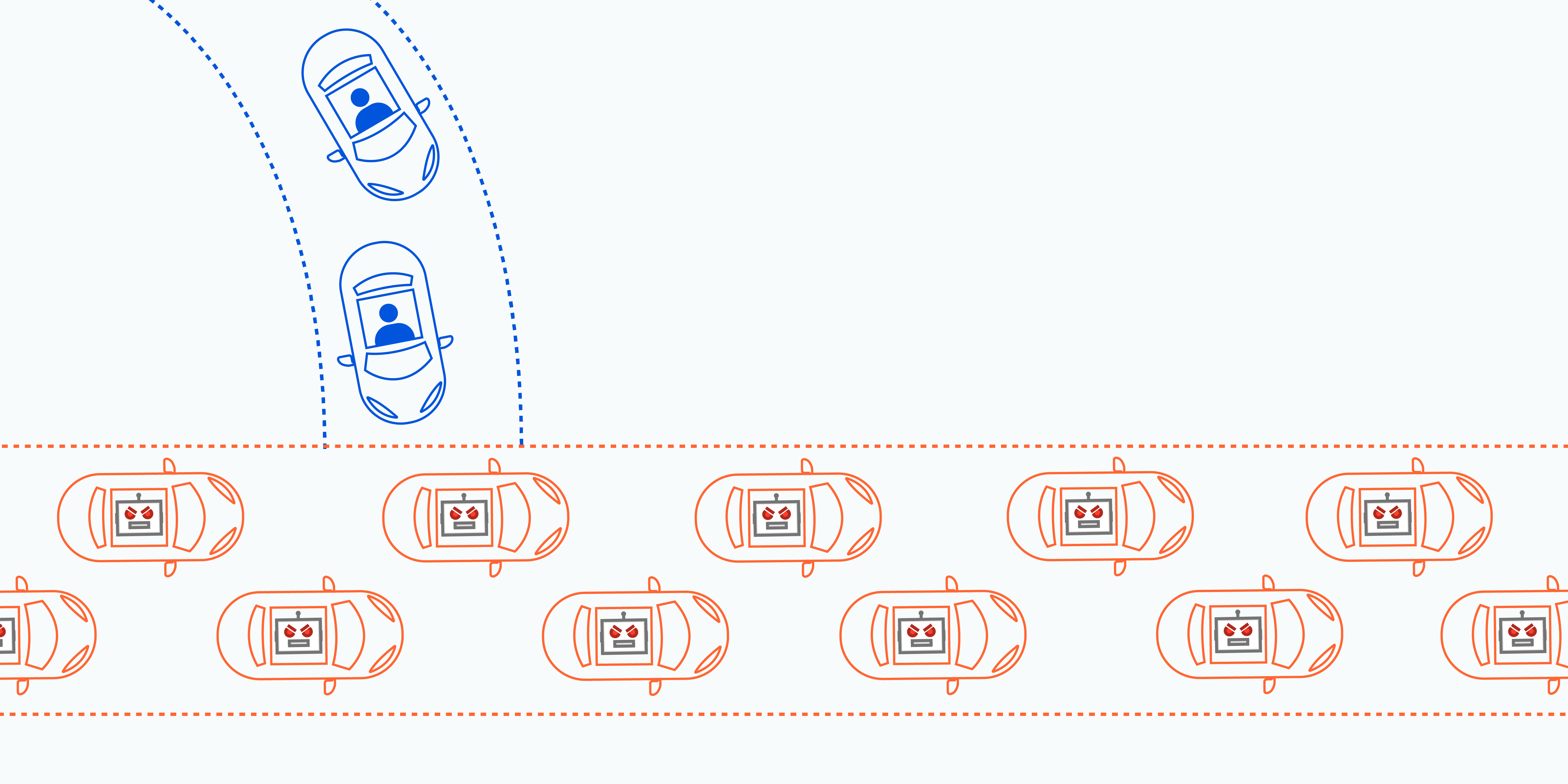
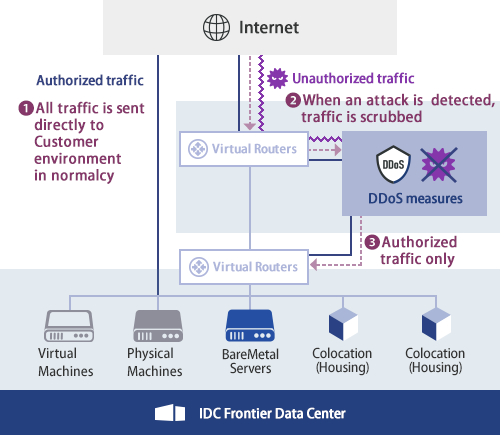
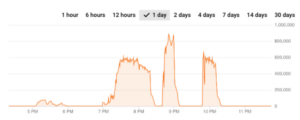
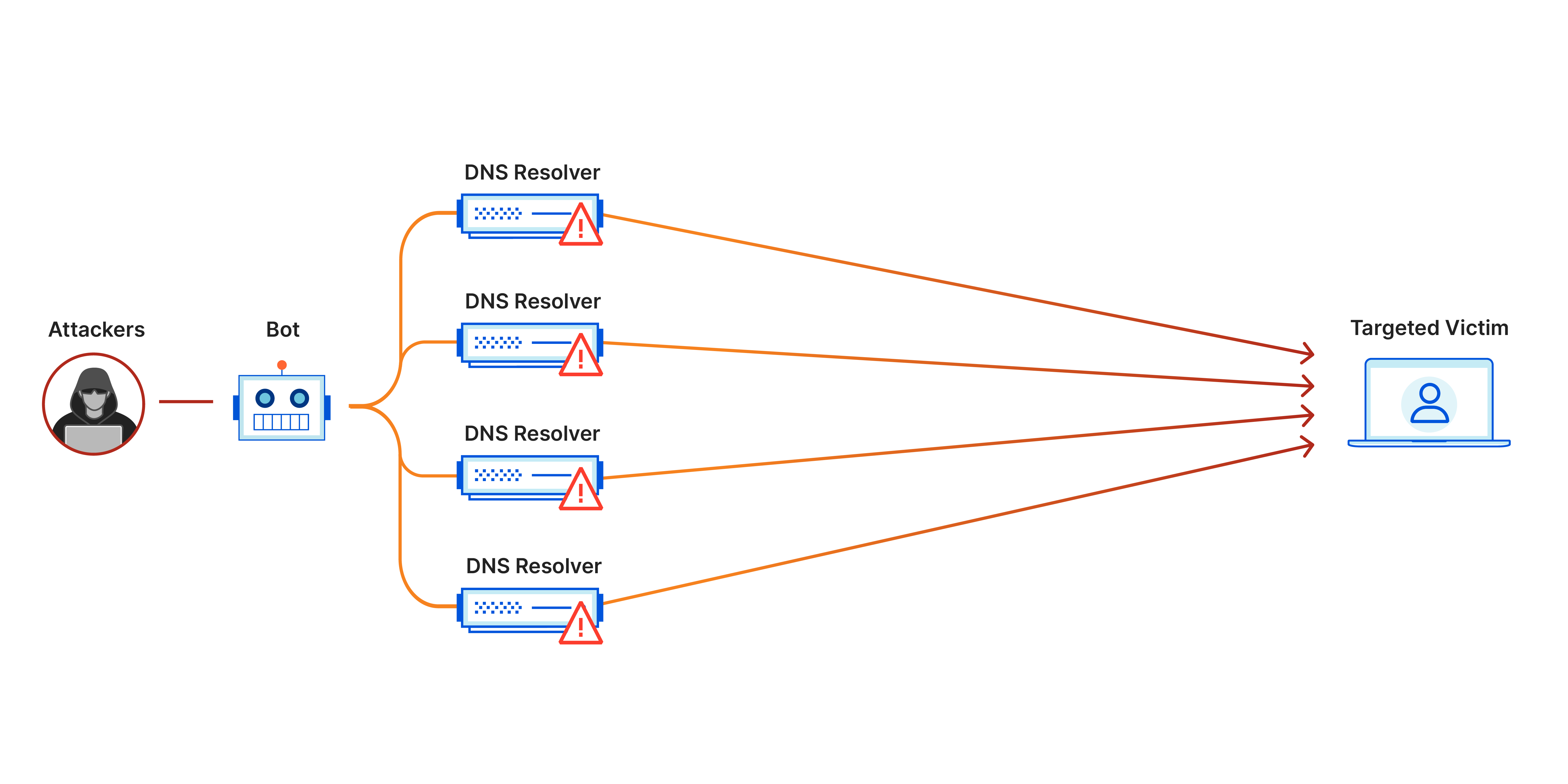
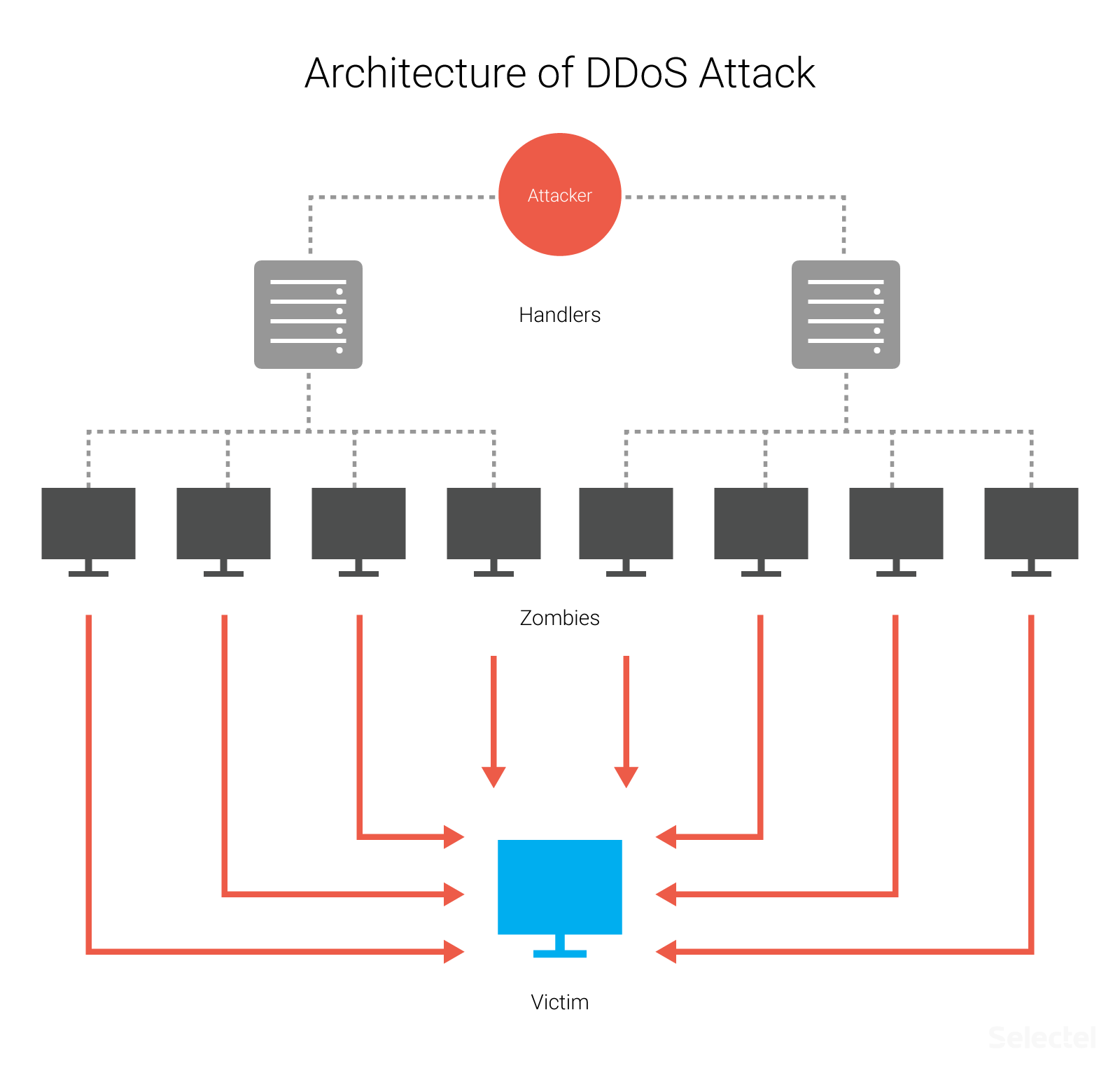
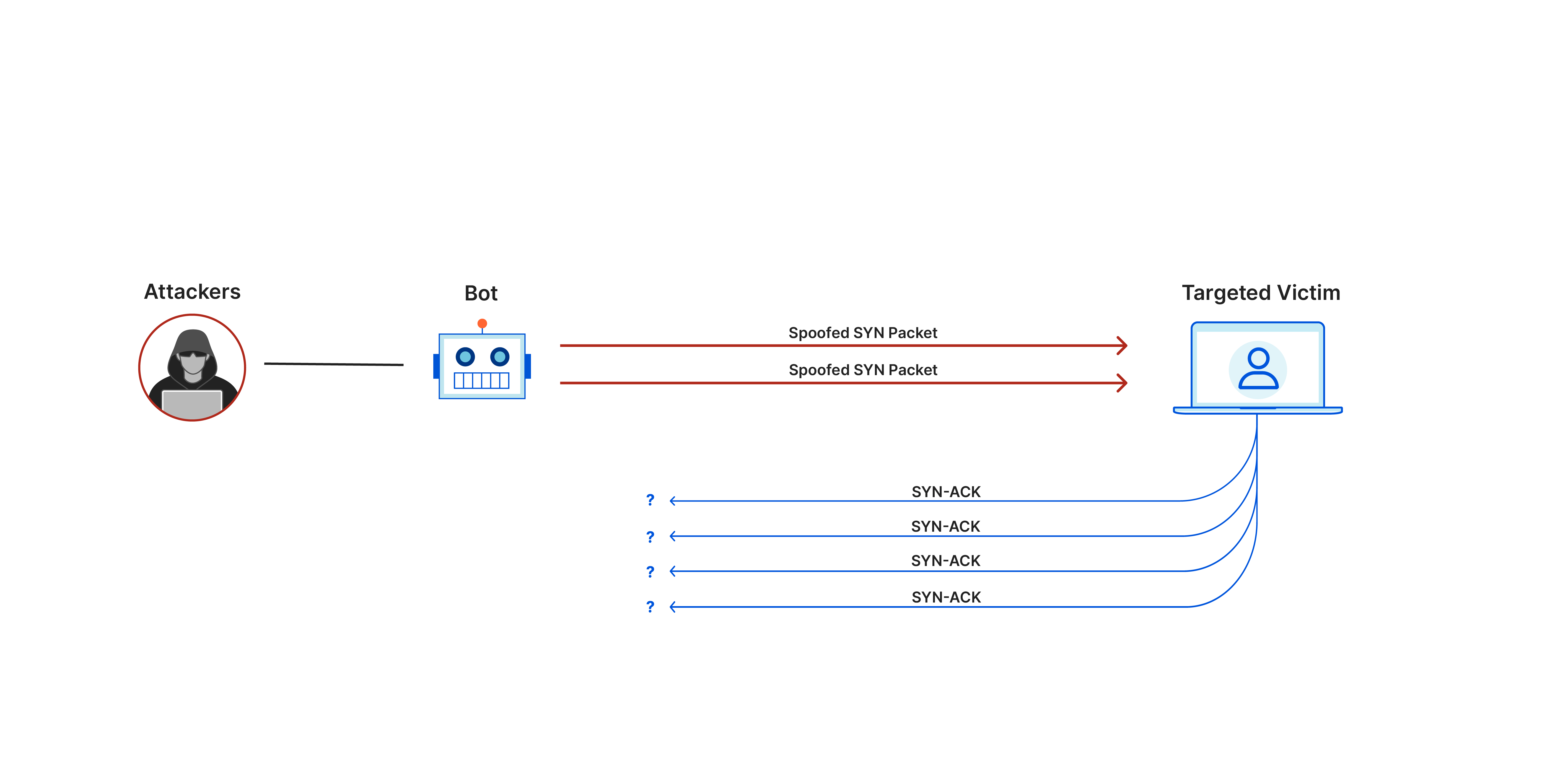
A DDoS attack detection and countermeasure scheme based on DWT and auto-encoder neural network for SDN - ScienceDirect
Defending against TB-level Traffic Attacks with Advanced Anti-DDoS systems - Alibaba Cloud Community

An overview of DDoS attacks, each with a description and countermeasures | Download Scientific Diagram

Symmetry | Free Full-Text | Detection of Adversarial DDoS Attacks Using Generative Adversarial Networks with Dual Discriminators
![PDF] Scope of DDoS Countermeasures : Taxonomy of Proposed Solutions and Design Goals for Real-World Deployment | Semantic Scholar PDF] Scope of DDoS Countermeasures : Taxonomy of Proposed Solutions and Design Goals for Real-World Deployment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/289f14f55e856fbd41dc4c299ce0f205ff094f26/2-Figure1-1.png)