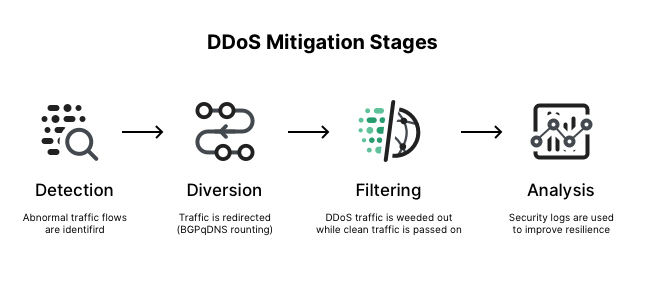
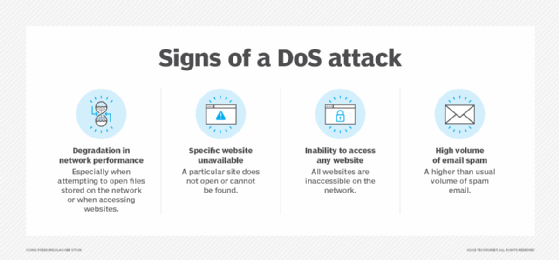
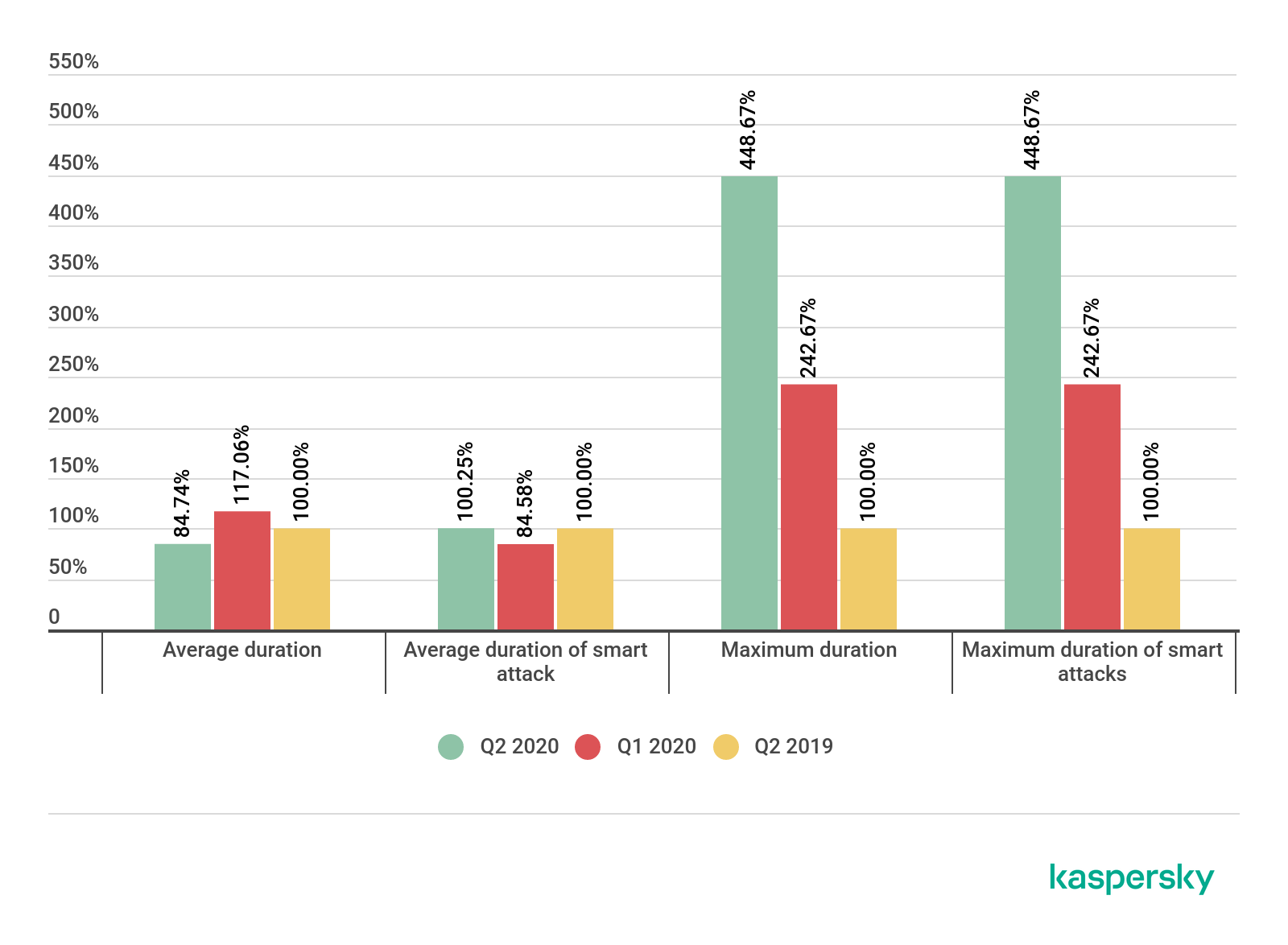
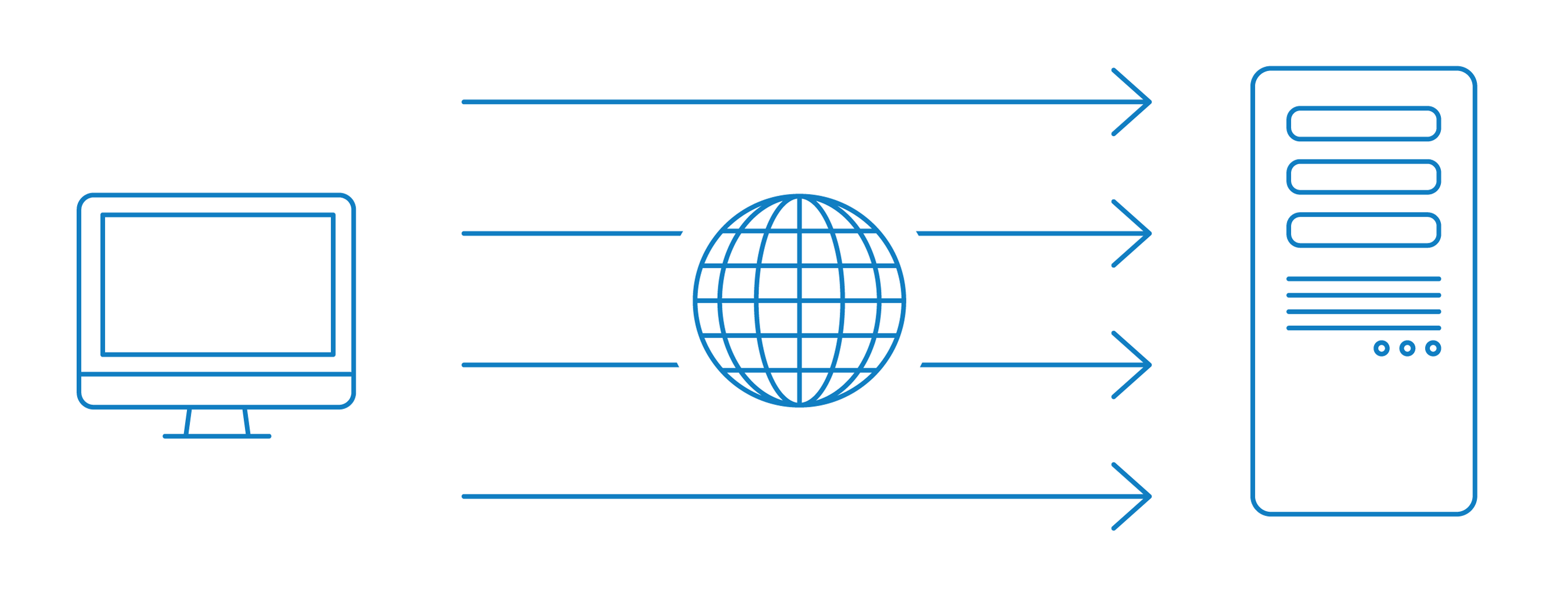
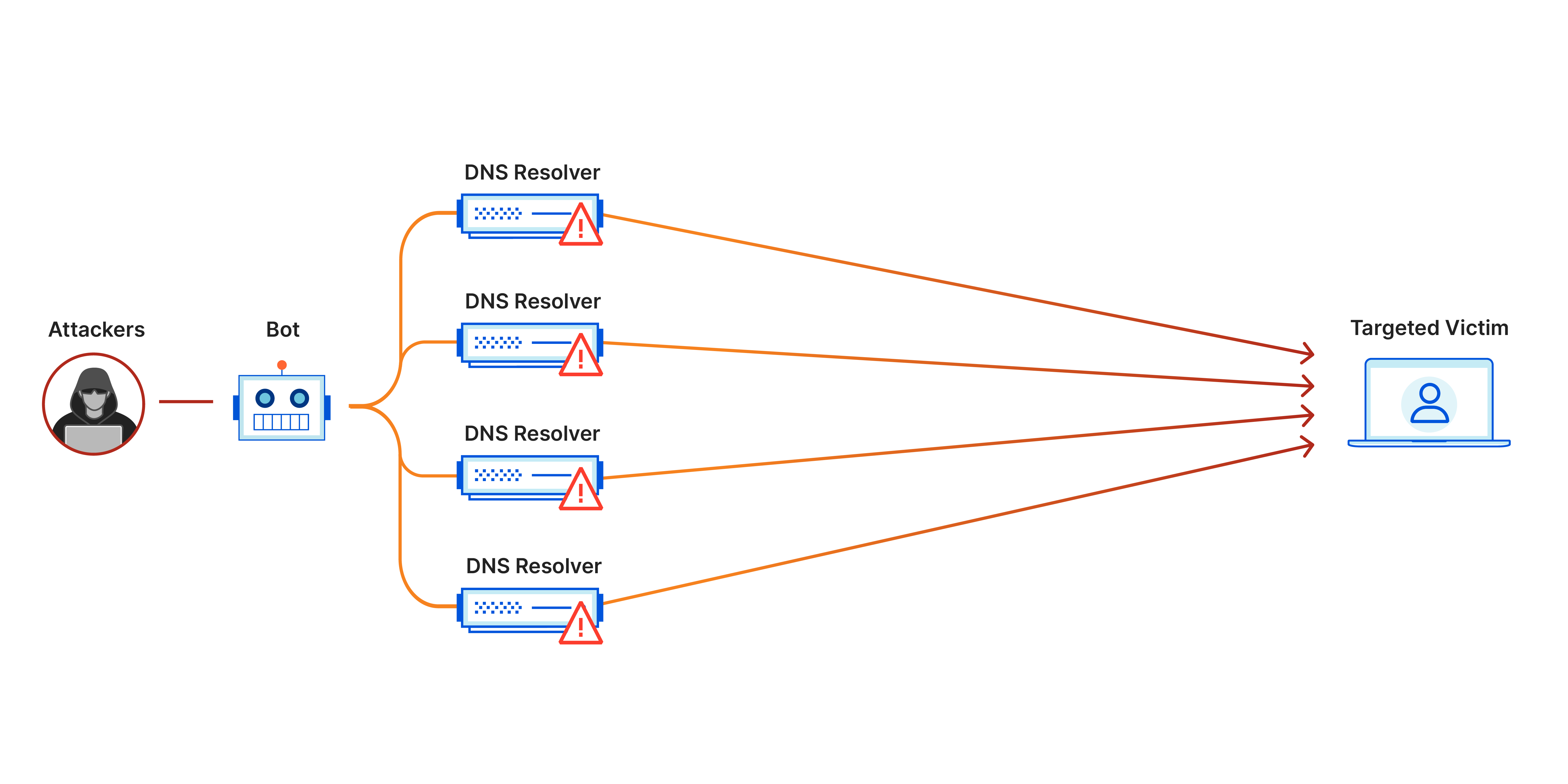
Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing Base on RFC 2827 Lector Kirill Motul. - ppt download
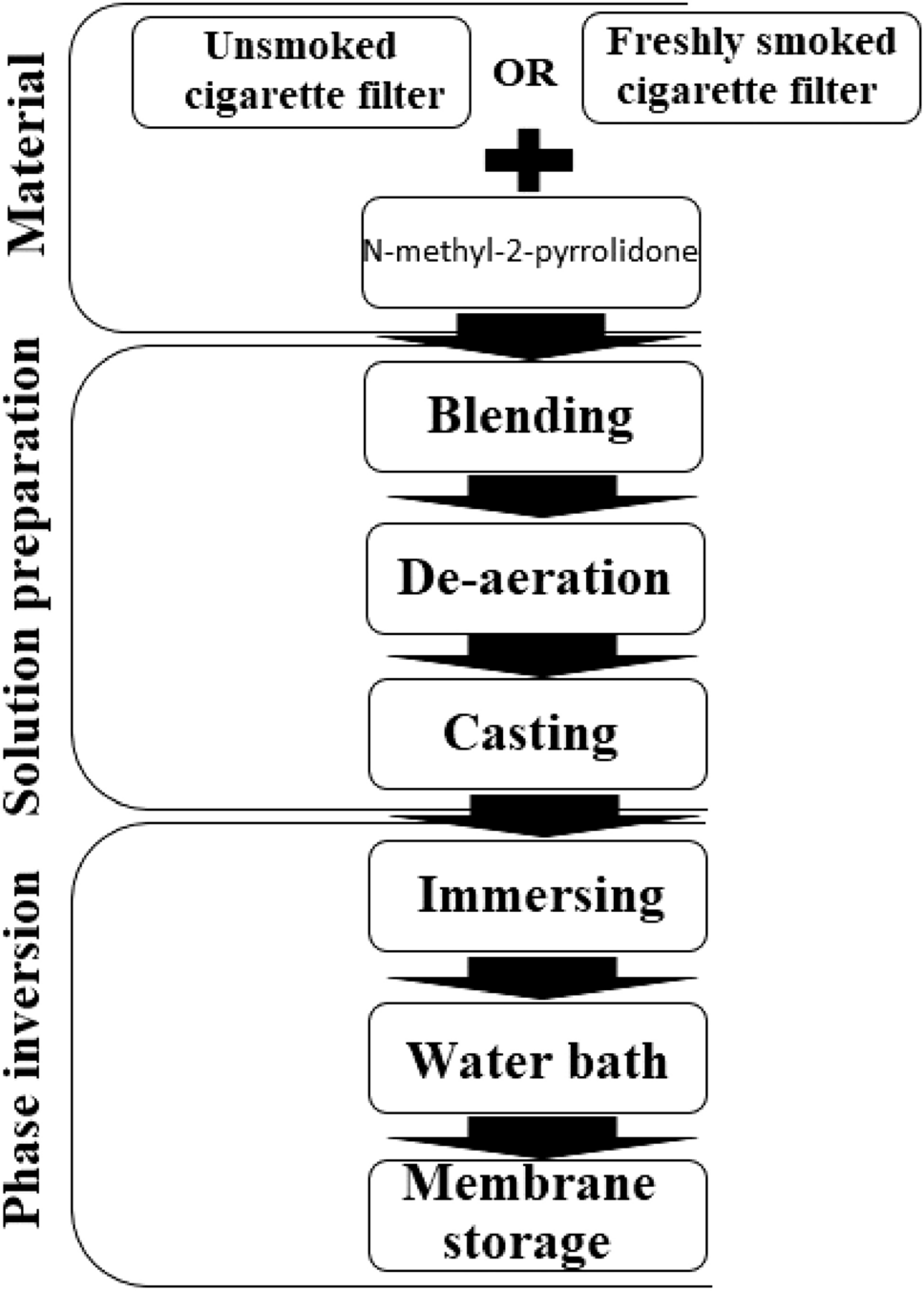
Preparation of a cellulose acetate membrane using cigarette butt recycling and investigation of its efficiency in removing heavy metals from aqueous solution | Scientific Reports
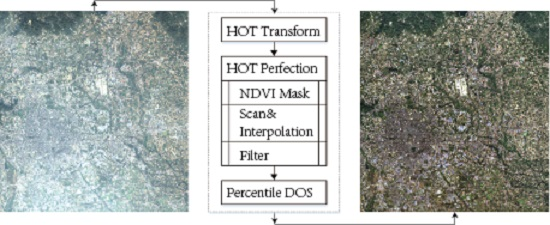
Remote Sensing | Free Full-Text | A High-Fidelity Haze Removal Method Based on HOT for Visible Remote Sensing Images



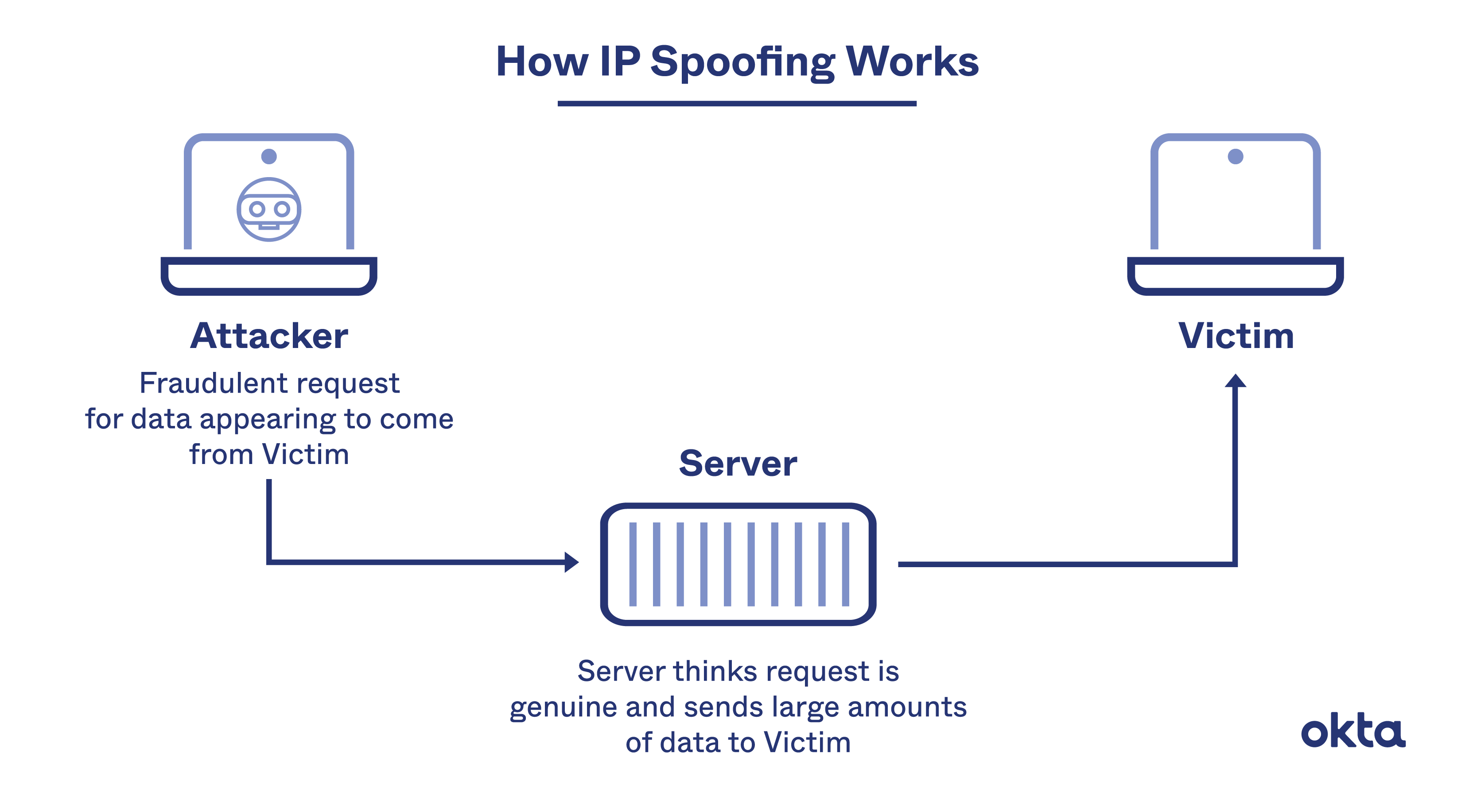

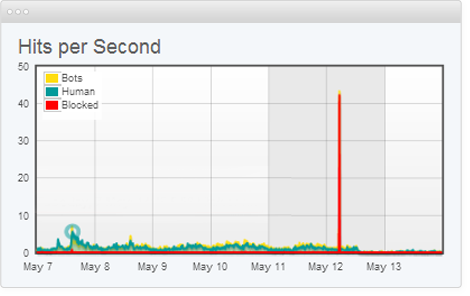

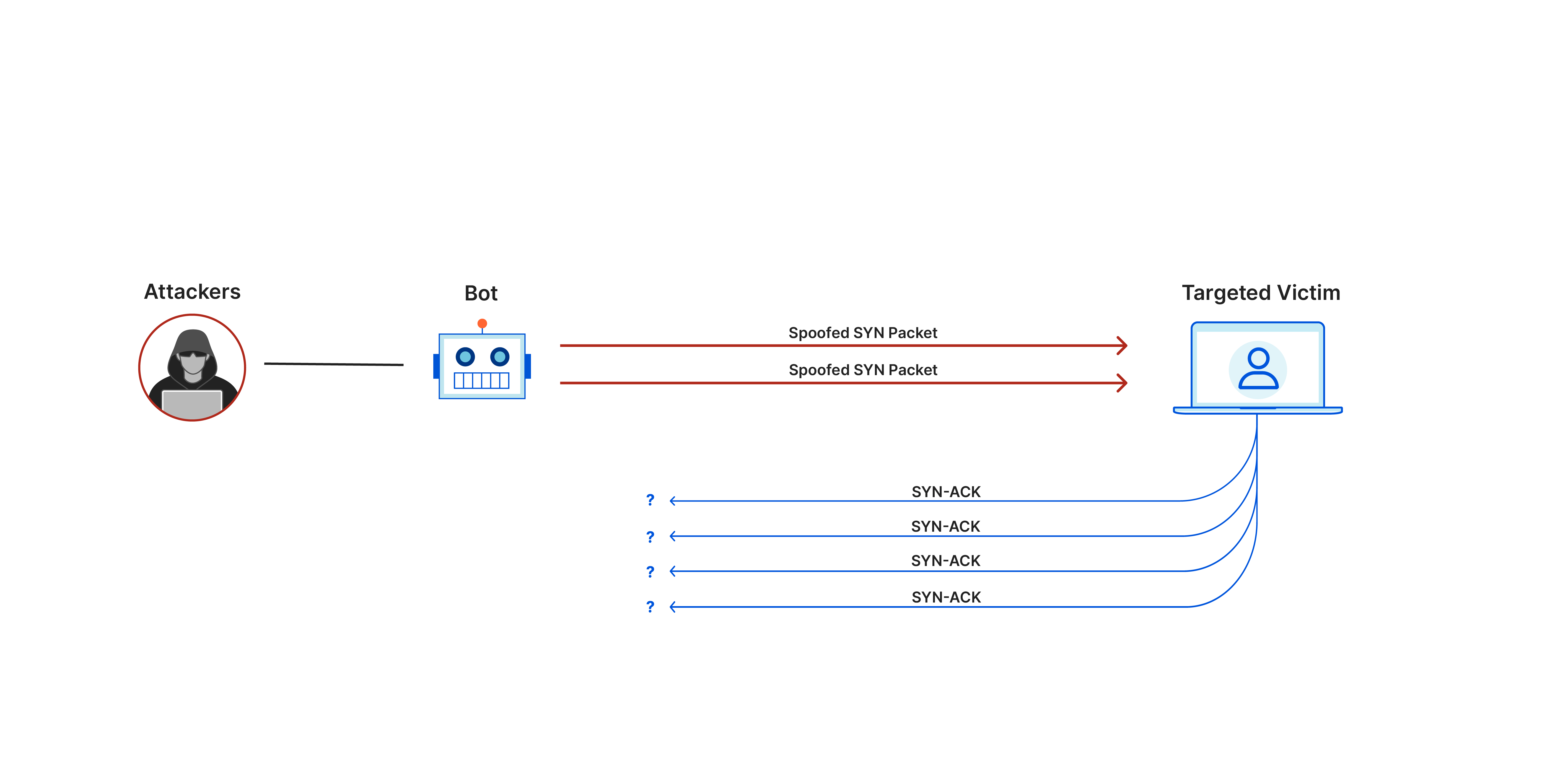



![PDF] A Review of DOS Attacks in Cloud Computing | Semantic Scholar PDF] A Review of DOS Attacks in Cloud Computing | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/71cfe635a8596afe483991ab5830221ec92abcbb/3-Table1-1.png)